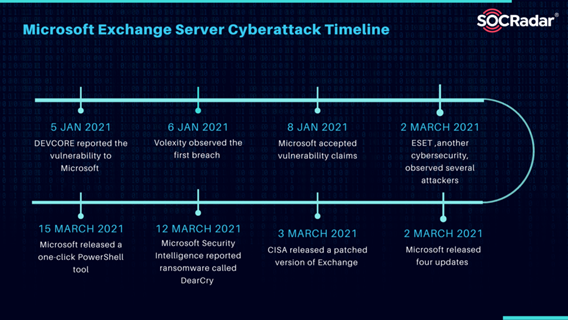
In Jan 2021, a global wave of cyberattacks and data breaches began after four zero-day exploits were discovered in on-premises Microsoft Exchange Servers. The result of these attacks ended in granting them full access to affected servers, user email passwords, and other details.
Microsoft detected the attack on March 2, 2021, when they had to witness many attackers. They detected a series of zero-day exploits as the attack occurred on-premises versions of Microsoft Exchange Server. It was the beginning of cyber threats lingering on organizations across the United States.
The attackers were holding onto many vulnerabilities and exposing the data of organizations that had not updated their software. In this article below, we will discuss the timeline of the attack and also suggest solutions to avoid any of these threats in the future.
The Timeline of the Microsoft Exchange Server Hack
As technology has advanced, more businesses are relying more and more on technology. But there comes a bigger threat, and server attacks from Microsoft showed that to us, and we know now. Let’s talk about the timeline and how leaving your software outdated can cause you these troubles such as loss of data including: personal data and customer data. Or else how to have solid solutions for it. Let’s start.
The attacks were carried out by the previously unknown Chinese hacking group known as Hafnium. The IT giant’s Threat Intelligence Center (MSTIC) assumed Hafnium was state-sponsored and operated from China. Notably, their primary concentration was on enterprises in the United States across a variety of industry sectors. Hafnium used leased virtual private servers (VPSs) in the United States, adding a degree of complexity to their cyber activities.
When attackers penetrate Microsoft Exchange, they send automatic commands to extract all emails from servers as well as users’ passwords and email addresses, which are stored unencrypted in memory. This vulnerability allows attackers to add backdoors to vulnerable systems, get access to non-exploitable systems on the same network, and install ransomware. While the Exchange server was patched against the attack, installed backdoors were not removed. Failure to eliminate additional backdoors and unauthorized user accounts added by attackers means continued unauthorized access to the system.
On March 2, 2021, Microsoft provided fixes for 2010, 2013, 2016, and 2019 that addressed the exploit. Four Microsoft Exchange Server versions (2010, 2013, 2016, and 2019) were identified as vulnerable to cyberattacks, however the exact editions remain unknown. Cyberattacks do not disrupt cloud-based services like Exchange Online or Office 365.
Over the next few days, the attacks affected over 30,000 companies in the United States, demonstrating the scope of the breach. Hackers used the weaknesses to snoop, infecting around 250,000 servers. The offensive targets disease researchers, law offices, universities, defense contractors, non-governmental groups, and think tanks.
The attackers targeted on-premises servers, taking advantage of the low security of firms that had not moved to online exchanges. Gartner researcher Peter Firstbrook stated that the hackers sought a rich attack environment within less mature enterprises, where IT generalists administered Exchange, putting them vulnerable to missing critical upgrades.
Microsoft’s response included the provision of comprehensive patches to address the reported vulnerabilities. The company recommended enterprises implement these updates as soon as possible to reduce the risks posed by the Exchange Server attack. The event demonstrated the necessity of keeping security protocols up to date, particularly in systems that use legacy software.
The Hackers' Endgame
 Firstbrook underlined that the hackers’ goals extended beyond compromising on-premises servers. Instead, they aimed to build a strong assault infrastructure for future operations against higher-value entities linked to the infected systems. By penetrating less protected businesses, the hackers set themselves up to execute complex attacks against interlinked, high-profile targets. This method made it difficult to detect and identify threats because the attackers hid their operations within ostensibly genuine communications.
Firstbrook underlined that the hackers’ goals extended beyond compromising on-premises servers. Instead, they aimed to build a strong assault infrastructure for future operations against higher-value entities linked to the infected systems. By penetrating less protected businesses, the hackers set themselves up to execute complex attacks against interlinked, high-profile targets. This method made it difficult to detect and identify threats because the attackers hid their operations within ostensibly genuine communications.
Attackers were identified by obtaining all emails from certain users linked to Microsoft Exchange servers. Washington think tanks reported that attackers used persuasive emails in a social engineering attack to get users to click on a link. Norway’s parliament stated on March 11, 2021, that it had been the target of an attack, with threat actors extracting its data. Additionally, the European Banking Authority was targeted in the hack.
On March 12, 2021, Microsoft Security Intelligence revealed that ransomware named DearCry was spreading on computers by encrypting device contents and rendering servers inoperable. After that, DearCry sought payment to recover files. However, Microsoft says there is no guarantee that paying the ransom will get you access to your information.
Get in Touch
Finally, it served as a wake-up call for businesses to prioritize cybersecurity and remain watchful against future threats. The incident also highlighted the necessity for continued education and awareness campaigns about the importance of frequent software upgrades and security measures in protecting against sophisticated cyberattacks. So, if you are running a business, you must start protecting your data right away.
As you roll out new technologies, you need cybersecurity. We at DHRP can help you deploy cybersecurity solutions and give insights you on Microsoft data breaches and Microsoft security services. You can find all the solutions services by exploring the tools provided by the DHRP through their trusted partner, ThreatLocker.
ThreatLocker has an immense number of cybersecurity features and fits large and small businesses at every step. In times of the possibility of emerging attacks, you must start taking steps towards protection and security. Reach out to us, and let’s see how we can help you with securing your systems.